Correct Answer
Multiple Choice
The company where Derek works has tasked him with setting up and securing a SOHO router. He wants to make sure the wireless network is secure and that no unauthorized person can gain access to the network. What is the first step Derek should perform to secure the wireless router?
A) Disable SSID.
B) Set encryption standard.
C) Check radio power levels.
D) Change default user name and password.
F) C) and D)
Correct Answer

verified
D
Correct Answer
verified
Matching
Match the protocol or encryption name with the feature.
Correct Answer
Multiple Choice
A corporate user is attempting to connect to the company's Windows domain server on the local network with her new laptop through a wired connection. Which of the following is required for the user to successfully sign in to the Windows domain?
A) SSID, authentication and encryption settings
B) Windows domain user name and password
C) A valid connection to a DHCP server on the LAN
D) User name and password supplied by the ISP
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is a scenario in which an IT support technician would most likely be required to implement the alternate IP configuration method on a network host?
A) To ensure a workstation receives the same IP address from the DHCP server each time the workstation is booted.
B) In the event a DHCP server is unavailable, the workstation will have a valid IP address on the subnet.
C) When a workstation requires that more than two different DNS server IP addresses be configured for a specific network interface.
D) To assign a secondary DNS server IP address to a specific network interface on the workstation.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician is configuring a new SOHO multifunction wireless router at a customer's location to provide network access to several wireless devices. The technician is required to protect the customer's private network from unauthorized access while performing the initial router setup as well as during normal operation after the configuration is completed. Which of the following is the best step for the technician to take in securing the router to meet this requirement?
A) Enable DHCP on the router and configure IP address reservations for the wireless clients.
B) Change the router's default administrative password.
C) Disable the router's radio in the wireless network settings.
D) Configure MAC filtering on the router and allow access to only the technician's computer.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Matching
Match the protocol or encryption name with the feature.
Correct Answer
Multiple Choice
A remote worker wants to connect his computer to his corporation's private trusted network over the Internet. Which of the following will need to be configured?
A) VPN tunnel
B) Address reservation
C) DHCP server
D) Firewall
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following will use an RJ-11 connector for connectivity?
A) Cellular
B) Cable
C) Fiber
D) DSL
E) Ethernet
G) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have connected an ADSL Internet connection as shown in the exhibit. The ports at the phone jack are connected to the same single-number POTS line.
At what location should you place the DSL filter?

A) "A" only
B) "A" and "B"
C) "B" only
D) "A" and "C"
E) "C" only
F) No filters are required
H) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
 What connector is shown in the exhibit?
What connector is shown in the exhibit?
A) USB-A
B) RJ-11
C) F-type
D) RJ-45
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are tasked with configuring a wireless SOHO router for a customer. Which of the following settings will be the most secure with the least effort and cost to the customer?
A) WPA2-Enterprise
B) WPA-PSK, TKIP
C) WPA2-PSK, TKIP
D) WPA2-PSK, AES
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are setting up your Windows computer to connect to the Internet and notice that when you type www.microsoft.com, the browser does not go to the site. Instead, you receive an error message saying that the address cannot be resolved. What network setting should you check to see the address of the server being used to resolve this address?
A) IP address
B) Subnet mask
C) Gateway
D) DNS
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A technician wants to configure a DHCP server to guarantee that certain printers always receive the same address. Which of the following should the technician configure?
A) VPN tunnel
B) Address reservation
C) Subnet mask
D) Default gateway
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Matching
Match the protocol or encryption name with the feature.
Correct Answer
Multiple Choice
A client is requesting an Internet connection type that is not affected by atmospheric conditions and is always on. Which of the following will meet these requirements?
A) Dial-up
B) Cable
C) Satellite
D) Cellular hotspot
F) All of the above
Correct Answer

verified
Correct Answer
verified
Matching
Match the protocol or encryption name with the feature.
Correct Answer
Multiple Choice
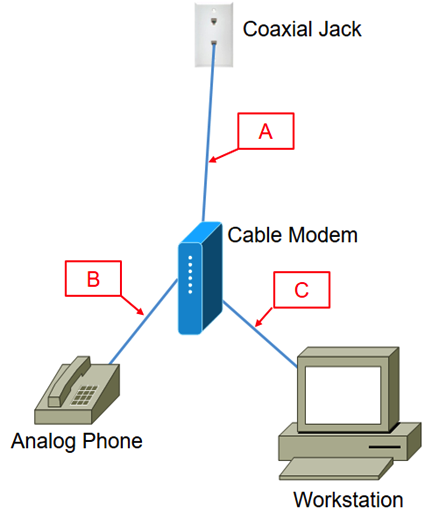 You have connected a cable Internet connection as shown in the exhibit.
At what location should you place a filter?
You have connected a cable Internet connection as shown in the exhibit.
At what location should you place a filter?
A) "A" only
B) "A" and "B"
C) "B" only
D) "A" and "C"
E) "C" only
F) No filters are required
H) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A manager in a small office is asking if it is possible to limit network access to a particular website during business hours. Apparently, several users are spending an excessive amount of time on the site preventing them from completing their work-related tasks. Which of the following is the best solution to accomplish the request from the manager while not limiting access to other websites?
A) Implement MAC filtering on the SOHO router for the PCs that are accessing the site.
B) Configure a firewall and add the site the users are visiting to the whitelist.
C) Configure a firewall with content filtering on the PCs of users who are visiting the site.
D) Implement a blacklist on the firewall and add the site the users are visiting.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have been tasked with configuring a SOHO network in which all ports on the public untrusted network will be forwarded to one workstation connected to the LAN. Which of the following features will you configure on the SOHO router to accomplish this task?
A) Port forwarding
B) MAC filtering
C) Demilitarized zone
D) Quality of service
F) C) and D)
Correct Answer

verified
C
Correct Answer
verified
Showing 1 - 20 of 35
Related Exams